Buffer Overflow
What is Buffer Overflow
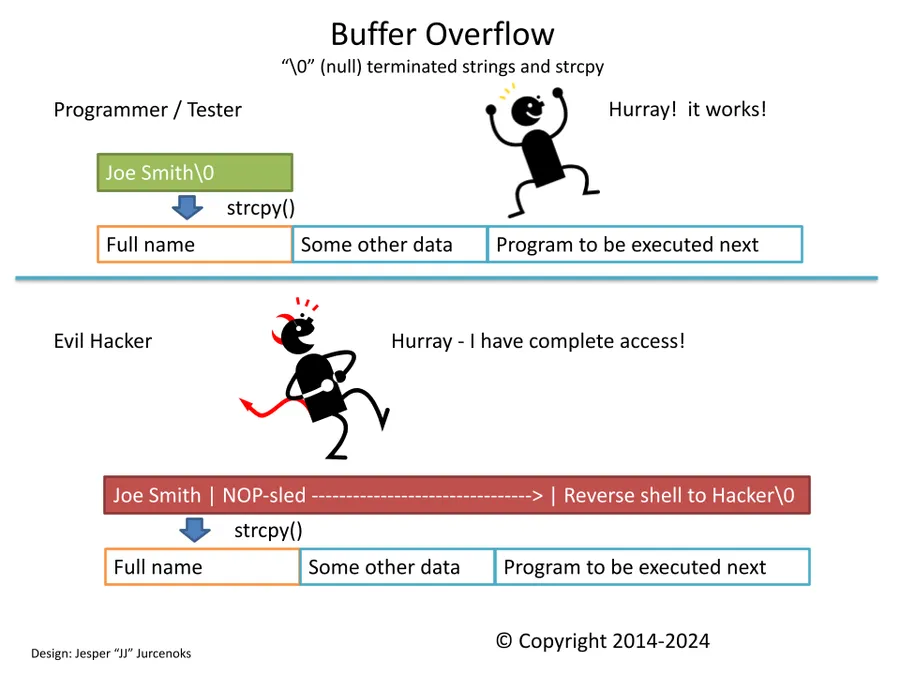
Buffer overflow Explained
- C/C++ uses Null terminated strings '\0', where other languages have the string length stored in a separate variable.
- The C/C++ function used to copy text from one string to another (strcpy) just keeps going until it finds a '\0'...
- It even keeps going past the end of the of the buffer...
- And keeps on going into some vital program area where the return address is stored...
- Then when the computer is trying to execute the overwritten return address the program will either: 1. crash (DoS) or 2. start executing the code placed by the attacker via the oversize source string (Remote Execution)
- If the exploited program has Admin privileges then it is GAME OVER and the victim computer has been completely "pwned" (pronounced "owned")
- A length of No-Operation instructions (NOP-sled) can be used to catch program execution when start position is not precisely known and lead program execution to the attack code
Detecting Buffer Overflow
- Law-Enforcement informs you that your machine was used as an attack bot - Ouch (in 2013 70% of data breaches were discovered by external parties)
- Manual Code Review - Yuk! Mind numbing and takes forever, due to the human element not very reliable for large amounts of code. Use this once you have located the vulnerability using other means.9 Only works where you have the source code.
- Fuzzing / Fuzz-testing - Input designed to break your application. Protocol specific testers are easier to use and setup than more general tools. This works for programs where you don't have the source code.
- Automated Code Review - This is effective if you have access to the source code. There are a number of free tools available. Also called Static Application Security Testing (SAST)
- Binary code Analysis - Static or Dynamic code analysis of compiled applications for security flaws - very few players in this space.
- Vulnerability Assessment (VA) This is the fastest and easiest way to find 3rd party applications with known buffer overflows. Coolest: Easy online solutions not requiring installation or training.
- Penetration testing - Like Vulnerability Assessment but more intrusive - tries to exploit the buffer overflow to prove it. (fewer false positives)
Buffer Overflow Prevention
- C/C++ are the primary languages that lacks boundary checking - use almost any other language
- In C/C++ avoid using functions such as strcpy(), strcat(), sprintf(), vsprintf(), and gets() as these functions lack bounds checking and operate on null terminated strings.
- Use Safe libraries, replace your string handling with vetted safe libraries
- Disallow execution of instructions from buffer. Can be bypassed in some circumstances
- Use stack cookies to ensure that contents of the stack remain unchanged. like Stack Frame Canary Validation^SFCV
- Use a compiler with integrated security checks and buffer overflow detection to help avoid unsafe coding practices
- Address space layout randomization (ASLR) can help decrease the probability of buffer overflow by changing addresses dynamically upon reboot.Can be bypassed in some circumstances
- Use Secure Development Life-cycle (SDLC) including code analysis tools